July 9th — What Does It Mean to You?
You’ve probably heard about the FBI doing something in July that will affect thousands of Internet users, and may disrupt their ability to access many web sites, at least temporarily. Thankfully, due to a months-long publicity effort, most people have heard about this July date. But… most people still haven’t followed the instructions to first, check to see if they’re affected, and secondly, clean their computer if necessary.
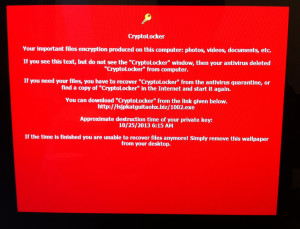
If you’ve been paying attention to the news articles, you know that the culprit is a trojan malware generically known as DNSChanger. This infection is in the Zlob family of trojan viruses, and is typically installed from trying to watch a video that supposedly needs a new video codec, that it informs you needs to be installed. What it actually installs is a rootkit virus. (Rootkit is geekspeak for a multi-faceted toolkit that accomplishes numerous tasks, while taking control of your PC.) The most obvious effect you will see is a suspicious warning that “YOU ARE AT RISK,” and you need to let some previously unknown antivirus scan your PC, after which it will issue dozens of warnings, and ask that you purchase a license to clean these “threats.” If you cooperate with the attack, you will hand some $30 to $80, plus your credit card information to the Russian or Ukrainian mob.
What are less obvious are the other tools in the rootkit’s bag. You probably now have a keylogger recording every key and login/password combination you type, along with a backdoor server to let remote criminals access this text data. Then comes the aforementioned DNS Changing aspect that reroutes your PCs Internet traffic from legitimate sites, to infected sites that continually reinstall the viral payload should your real antivirus program be capable of quarantining the initial infection. It may also attempt to access your household router in order to point that device’s DNS setting to the same crime-syndicate-controlled servers that were originally based in Estonia.
That was until the FBI and international police agencies arrested some of this particular gang of fraudsters, seizing those DNS servers and pointing their IP addresses to new FBI-run legitimate servers. It is this DNS service that the FBI is ending on July 9th. They are just not in the Internet Domain Name Server business.
It’s my experience that few of my customers would be able to use a Zlob-infected PC for long. They’ve usually contacted me within hours of first becoming infected with the malware. Others, though, may have a shared family desktop PC that has become infected, but individual members of the family no longer bother with it because it’s too slow. Thus, it’s happily humming along, sitting there as part of an international botnet (group of infected client computers controlled by remote commands.) If this sounds like your household, do everyone a favor and turn off the infected PC now.
Self Help
In the last few weeks both Google and Facebook have been alerting users of DNS-compromised PCs that their machines have problems. You should also visit: http://www.dns-ok.us/ This site will inform you if your DNS server settings are suspect.
Then, if need be, take a look at cleaning suggestions on this page: http://www.dcwg.org/fix/ Because of the Bootkit aspect of the infection, you’ll probably want to scan with more than one of the recommended anti-malware tools.
Medfield Computer Guy
Anyone in the metrowest Boston MA area can contact me here.
So, what can Medfield Computer Guy do for you that you can’t do yourself?
I can remove the virus and rootkit, and restore your PC and/or router’s DNS settings to their original configuration. Also, besides the Zlob trojan, there are other Fake Antivirus malwares that try to hide all your files and folders; they may also also destroy all your application shortcuts. I should be able to restore all your files, folders, and application shortcuts, after removing the virus from your computer. Then I’ll help you choose anti-malware software to keep you virus-free in the future. I’d be delighted to help you any time from now to July 9th, and well beyond.
Medfield Computer Guy
P.O. Box 122
Medfield, MA 02052
www.medfieldcomputerguy.com
(phone 508-359-8490)